WELCOME TO MY SOFTWARE NOTES !
to make interaction with content easier:
- make data flow diagrams of fun things like other neocity websites
- make sql queries for databases on like my friends or something
revision tips:
- review definitions
- work on charts and models
- AI and ML
add
- cyber attacks
Secure coding practices
Data validation - In secure software development, data validation is the process of validating input data and checking that it meets certain requirements. This helps prevent malicious attacks such as XSS and SQL Injection.
Data sanitization - is the process of reviewing input data and confirming that it contains no potentially harmful characters that could raise issues in the code.
An Injection attack - is a method of attack that sends inputs that intend to confuse and exploit the software system. SQL Injection is a form of Injection attack. Injection attacks can be very complicated and are difficult to prevent.
Machine learning problem types
- Classification (e.g. classifying emails)
- Regression (e.g. predicting house prices
- Clustering (e.g. segmenting customers on behaviour)
- Recommendation (e.g. recommending products for customers)
- Time series (e.g. predicting stock prices)
Model training
Depending on the ML problem type:
| Problem Type | Example Use Case | Common Algorithms |
|---|---|---|
| Classification | Spam email detection | Decision Trees, Random Forest, Neural Networks |
| Regression | Predicting house prices | Linear Regression, XGBoost |
| Clustering | Grouping customers by behaviour | K-Means, DBSCAN |
| Recommendation | Netflix | Singular Value Decomposition (SVD) K-Nearest Neighbours (KNN) |
| Deep Learning | Image recognition | Neural Networks, Transformers (e.g., BERT, GPT) |
Secure software architecture
Storing Sensitive Data: When storing sensitive data in a database or a file, encrypting the data ensures that even if the storage is compromised, the data remains unreadable without the decryption key.
Secure Communication: Encrypting data before sending it over a network ensures that even if the data is intercepted, it cannot be read by unauthorized parties. The encryption key, which is needed by the authentic receiver for decrypting the data, would be sent to the intended recipient in a separate transmission.
Secure Configuration Files: Encrypting configuration files that contain sensitive information like API keys, database credentials, etc., ensures they are not exposed if the files are accessed by unauthorized users.
Data Integrity Verification: Encrypting data along with a timestamp or a hash can ensure that the data has not been tampered with when it is decrypted.
Key Management: Securely storing and managing encryption keys is crucial. Developers can use key management services (KMS) provided by cloud providers (e.g., AWS KMS, Google Cloud KMS) or hardware security modules (HSM).
Access Control: Ensure that only authorized parts of the application and users have access to the encryption and decryption processes.
Regular Audits: Periodically audit the encryption process and key management to ensure compliance with security policies and standards.
1. Broken Access Control
Access control enforces policy such that users cannot act outside of their intended permissions. Failures typically lead to unauthorized information disclosure, modification, or destruction of all data or performing a business function outside the user's limits. Examples include: Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or users, but is available to anyone. Bypassing access control checks by modifying the URL or the HTML page. Permitting viewing or editing someone else's account, by providing its unique identifier Elevation of privilege. Acting as a user without being logged in or acting as an admin when logged in as a user.
2. Cryptographic Failures
Cryptographic failures are typically because of a weak encryption mechanism. It may be by weak or obsolete encryption algorithms, sloppy key management or not encrypting sensitive data at all.
3. Injection
Injection vulnerabilities occur when untrusted data is sent to an interpreter as a part of a command or query. Examples are SQL and LDAP injections. Note: SQL (Structured Query Language) is used to access and manipulate data in a database. We will be looking at this in detail later in the HSC course. Such vulnerabilities are exploited by attackers to perform unauthorized actions by running arbitrary commands or accessing data.
4. Insecure Design
This vulnerability arises when security is not considered from the beginning of application development. It can manifest in many ways, from insecure workflows to lack of basic security controls, creating vulnerabilities that are difficult to fix once the application is up and running.
5. Security Misconfiguration
Security misconfiguration occur when default securities are not defined or implemented. Causes of this include: missing appropriate security hardening across any part of the application improperly configured permissions on cloud services unnecessary features are enabled or installed (e.g., unnecessary ports, services, pages, accounts, or privileges) default accounts and their passwords are still enabled and unchanged error handling reveals overly informative error messages to users
6. Vulnerable and Outdated Components
Using components with known vulnerabilities puts the security of the whole application at risk. Causes of this include: developers not knowing the versions of all components being used by the the software application the software is vulnerable, unsupported, or out of date vulnerabilities are not scanned for regularly fixes, patches or upgrades not applied in a timely manner
7. Identification and Authentication Failures
These incidents are failures of user identification and proof authentication which can occur if the application: permits automated attacks such as credential stuffing, where the attacker has a list of valid usernames and passwords permits brute force or other automated attacks permits default, weak, or well-known passwords, such as "Password1" or "admin/admin" uses weak or ineffective credential recovery and forgot-password processes, such as "knowledge-based answers," which cannot be made safe uses plain text, encrypted, or weakly hashed passwords data stores has missing or ineffective multi-factor authentication displays the session identifier in the URL reuse a session identifier after successful login does not correctly invalidate Session IDs - user sessions or authentication tokens aren't properly invalidated during logout or a period of inactivity.
8. Software and Data Integrity Failures
Software and data integrity failures relate to code and infrastructure that does not protect against integrity violations. An example of this is where an application relies upon plugins, libraries, or modules from untrusted sources, repositories, and content delivery networks. An insecure content delivery pipeline can introduce the potential for unauthorized access, malicious code, or system compromise. Many applications now include auto-update functionality, where updates are downloaded without sufficient integrity verification and applied to the previously trusted application. Attackers could potentially upload their own updates to be distributed and run on all installations.
9. Security Logging and Monitoring Failures
Poor logging/monitoring – this will make security breaches harder to detect and monitor as well. Without logging and monitoring, breaches cannot be detected and responded to. Examples include: events such as logins, failed logins, and high-value transactions, are not logged (recorded) warnings and errors generate no, inadequate, or unclear log messages logs of applications are not monitored for suspicious activity logs are only stored locally appropriate alerting thresholds and response escalation processes are not in place or are ineffective penetration testing and scans do not trigger alerts the application cannot detect, escalate, or alert for active attacks in real-time or near real-time.
10. Server-Side Request Forgery (SSRF)
This is a vulnerability that arises when an attacker can cause the server to generate arbitrary requests against other systems. In turn, this allows internal services and data to get exposed. SSRF flaws occur whenever a web application is fetching a remote resource without validating the user-supplied URL. It allows an attacker to coerce the application to send a crafted request to an unexpected destination, even when protected by a firewall, VPN, or another type of network access control list (ACL).
SQL
| Words | Description |
|---|---|
| SELECT | the field(s) or calculated values to be displayed (basically print) |
| FROM | the table(s) to be used |
| WHERE | the search criteria |
| GROUP BY | the field(s) used to group the returned rows |
| ORDER BY | the field(s) that determine the sequence of the displayed results |
Data Flow Diagrams
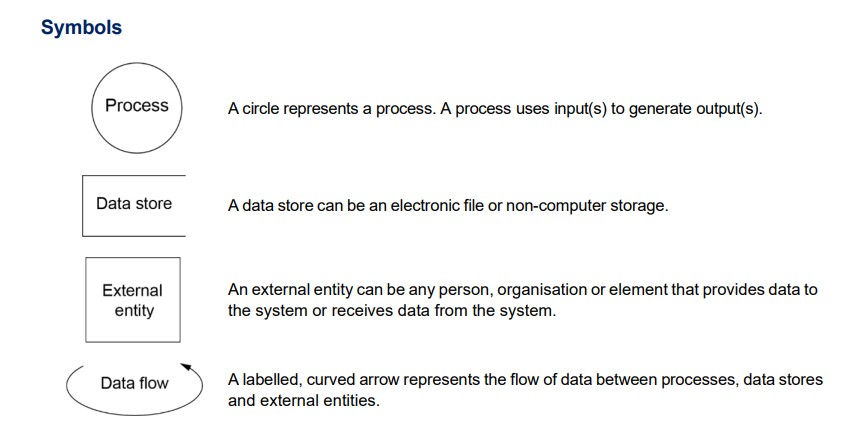
Symbols
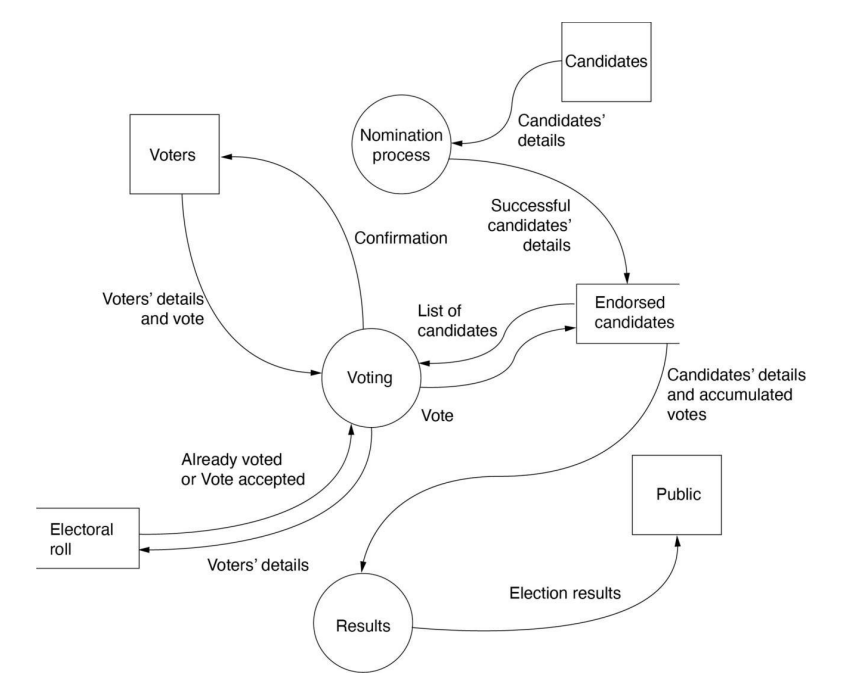
Level 1
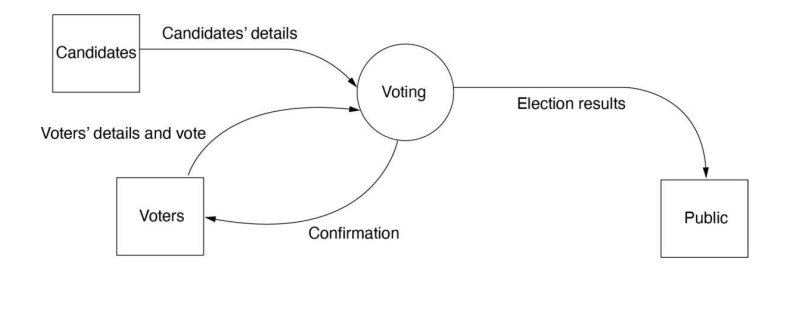
Level 0
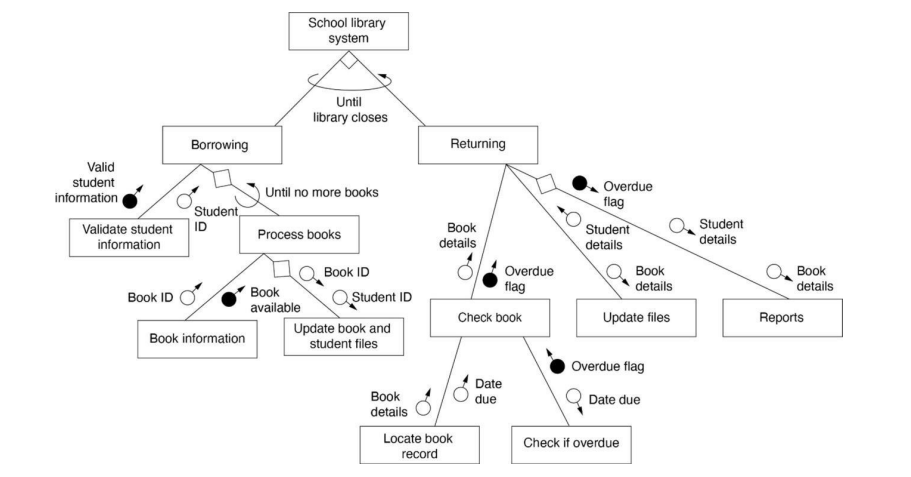
Structure Charts
Symbols

Structure Chart
Programming Paradigms
Object-oriented paradigm
Imperative paradigm
Logic paradigm
Function paradigm
Flowcharts
Symbols
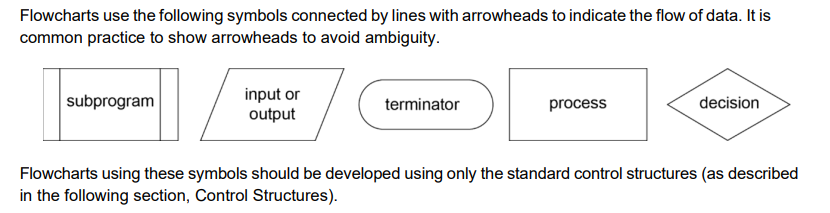
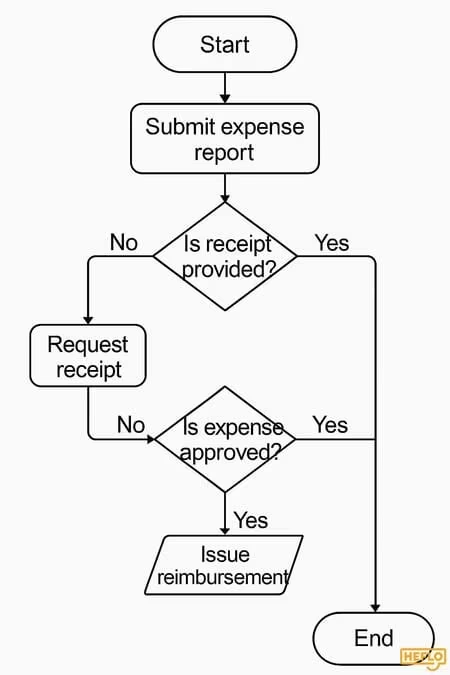
Flowchart
Pseudocode
- keywords are written in capitals
- structural elements come in pairs, e.g. for every BEGIN there is an END, for every IF there is an ENDIF
- indenting is used to identify control structures in the algorithm
- when refining the solution to a problem, a subroutine can be referred to in an algorithm by its name, with a separate subroutine developed with that same name to show the detailed logic.
Example

DevOps and MLOps
DevOps
DevOps is the joining of development(coding and design) teams and operation(maintenance) teams. It is the idea of both teams working together and communicating with eachother throughout a software project.
MLOps
MLOps is the automated process of designing, training, and deploying machine learning models. It follows similar principles to DevOps, where the teams for designing, training, and deploying a machine learning model work together and regularly communicate with eachother.
Cyberattacks
(information below was taken from ibm - cyber attacks)
Cross-site scripting (XSS)
XSS attacks insert malicious code into a legitimate web page or web application. When a user visits the site or app, the code automatically runs in the user’s browser, stealing sensitive information or redirecting the visitor to a malicious website. Attackers frequently use JavaScript to launch these exploits.
SQL injection
SQL injection attacks send malicious Structured Query Language (SQL) commands to the backend database of a website or application. Attackers input the commands through user-facing fields such as search bars and login windows, promhpting the database to return private data like credit card numbers or other customer data.
Protocols
TCP/IP (Transmission control protocol/Internet protocol)
- Creates IP addresses
- Specifies how data is exchanged over the internet and how it should be broken into packets
SMTP (Simple Mail Transfer Protocol)
- Used for sending and distributing outgoing emails
FTP (File Transfer Protocol)
- Used for transferring files from one system to the other
POP3 (Post Office Protocol 3)
- Retrieves and manages emails from the mailbox on the receiver mail server to the receiver’s computer
IMAP (Internet Message Access Protocol)
- Used for retrieving emails from a mail server
HTTP (Hyper Text Transfer Protocol)
- Used for communication over a computer network
TLS (Transport Layer Security)
- Encrypts data sent between a website and a browser